The center of gravity in AI is shifting from training to inference. Every stakeholder is asking to see ROI from their Enterprise AI investments, and inference is the means by which value can be driven.
However, Enterprise AI inference requires internal enterprise data to drive value. This creates an unprecedented security risk: previously segmented data spread across disparate silos is being centralized into knowledge bases to power applications - exposing a single point of breach for motivated attackers.
With this considerable security gap left unaddressed, Cyborg has built a solution using NVIDIA AI. The Cyborg Enterprise RAG Blueprint, available today on build.nvidia.com and GitHub, effectively resolves this challenge with CyborgDB, while maintaining best-in-class performance powered by NVIDIA Nemotron, NVIDIA NeMo Retriever™ microservices and NVIDIA accelerated computing.
The AI Centralization Paradox
76% of enterprises identify data security as the primary barrier to AI deployment (SAS, 2024).
The root cause isn’t traditional security concerns - it’s AI’s architectural requirements creating new systemic risks.
- RAG centralizes embeddings from across the enterprise into vector databases.
- This transforms fragmented data into concentrated, high-value targets.
- The result: a smaller attack surface with a much larger breach radius, giving attackers the unprecedented ability to access significant cross-sections of organizational data.
Furthermore, the vector embeddings themselves can be a source of vulnerability. Vector embeddings are not like hashed passwords, but more like compressed secrets. They are invertible - meaning attackers can reconstruct original sensitive content from compromised vectors, regardless of the original modality (e.g., text, images, audio). We've written about this, and so have security organizations like OWASP.
This creates the centralization paradox: the same consolidation that makes AI powerful also introduces the largest single breach risk enterprises have ever faced.
Encryption-in-Use: The Missing Security Layer
Traditional vector databases treat security as an afterthought - encrypting data at rest and in transit, but exposing plaintext during query execution.
Enterprise AI requires a fundamentally different approach: full encryption-in-use.
This is made possible by CyborgDB, our encrypted vector store. It performs three key functions: vector ingestion, vector search, and encrypted indexing.
The first two functions mirror those of standard vector databases - enabling high-performance semantic search through document and query embeddings. What sets CyborgDB apart is its third capability: encrypted indexing. This ensures that all inference-related data - embeddings, content, and metadata - remain encrypted throughout their entire lifecycle, from storage to retrieval.
By keeping sensitive data continuously protected, CyborgDB provides the foundational layer of security and trust required for deploying AI systems in enterprise environments.
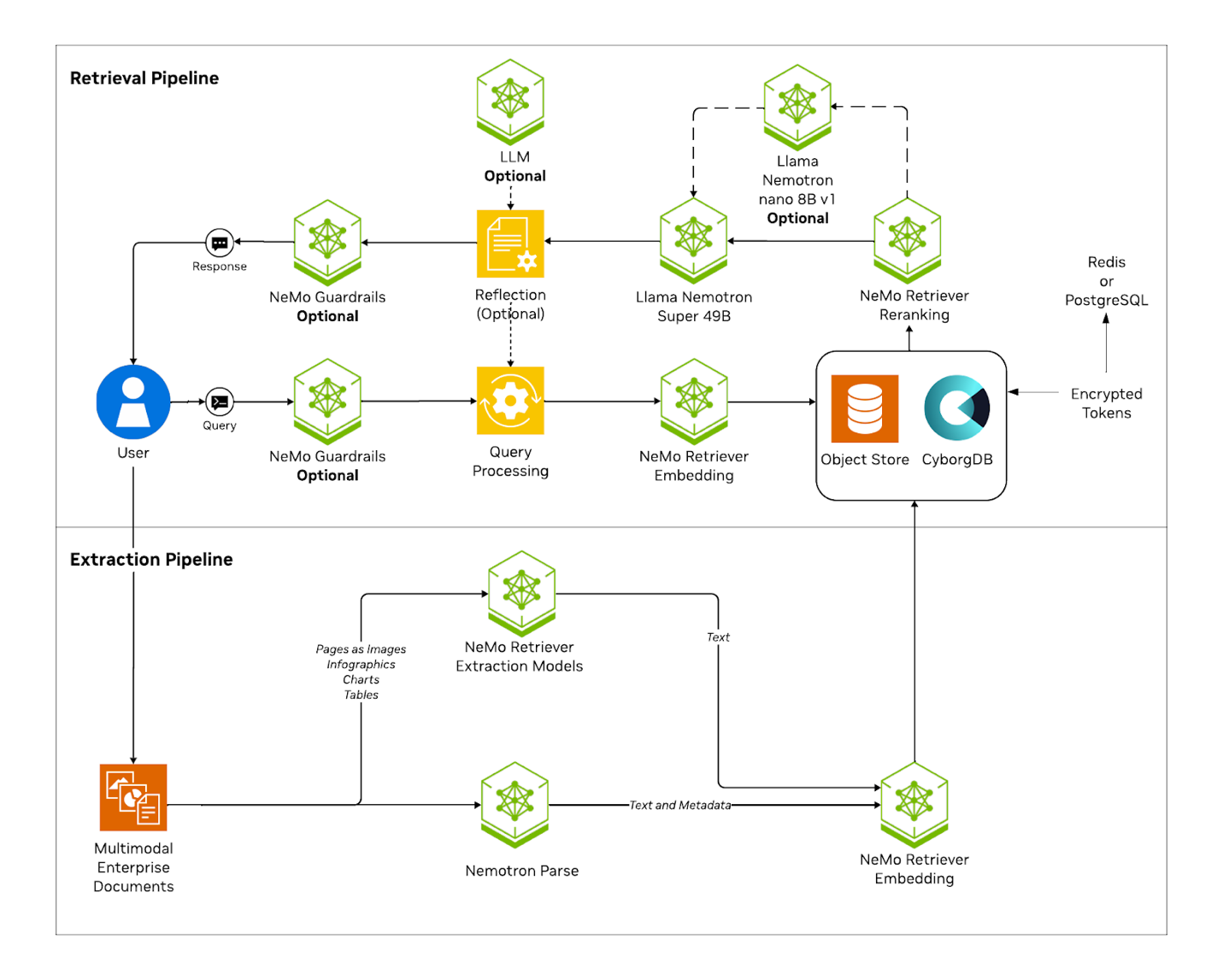
How the Cyborg Enterprise RAG Blueprint Works
Embedding Generation & Cryptographic Indexing
- User data is parsed and converted into embeddings using an NVIDIA NeMo Retriever embedding model.
- Embeddings are cryptographically indexed via CyborgDB, producing encrypted tokens.
- Encrypted tokens are stored in standard backing stores with vector search capabilities (e.g., Redis, PostgreSQL).

Encrypted Retrieval
- At query time, prompts are embedded and sent to CyborgDB for cryptographic retrieval.
- Plaintext never exists in memory, logs, caches, or during search.

Key Management
- Initial release: configuration file-based keys. The launchable notebook generates an encryption key once and stores it in base64 format on disk, which is then used as the index key.
- Upcoming update: first-party KMS integrations for major cloud providers.
To learn more about CyborgDB’s security and cryptography, see our Encryption Breakdown Guide.
Security Without Performance Compromise
Traditional security solutions often create unacceptable performance penalties. This blueprint proves the opposite.
Security Guarantees
- Zero plaintext exposure throughout application lifecycle.
- Forward-secure indexing prevents reconstruction attacks on historical data.
- Customer-controlled keys (BYOK/HYOK) - enterprises own encryption keys, not vendors.
Performance Gains with NVIDIA
- 47x faster indexing on 88M vectors (<1% encryption overhead).
- 7x higher query throughput for batch ops (<15% latency impact).
- Single-digit millisecond response times at scale, fully encrypted.
The Cyborg Solution
The blueprint leverages NVIDIA NIM inference acceleration with CyborgDB’s enterprise-grade encryption-in-use in a production-ready architecture that supports multimodal capabilities: including PDF parsing and advanced table and chart extraction, hybrid search, and reranking with NVIDIA NeMo Retriever.
The architecture leverages the NVIDIA software stack:
- NeMo Retriever for multimodal document parsing and embedding generation.
- Llama Nemotron 3.3 Super 49B for response generation.
- NeMo Retriever reranking reorders results by relevance, boosting answer accuracy and quality.
- NeMo Guardrails enforces AI safety and security, keeping responses accurate and appropriate.
- CyborgDB with NVIDIA cuVS acceleration for fast, secure encrypted vector operations.
This means enterprises benefit from high-performance, enterprise-grade RAG, plus CyborgDB's zero-plaintext security guarantees. The blueprint maintains full compatibility with LangChain integration patterns and OpenAI-compatible APIs that enterprises already use.
The key differentiator: cuVS GPU-accelerated encrypted search with automatic failover, enterprise key management integration, and the same sub-10ms query performance as unencrypted alternatives.
Financial Services
- Investment banks can unlock AI-powered research across trading models and client communications without exposing themselves to catastrophic breaches. Even if the database is compromised, attackers get nothing - the concentrated knowledge that makes RAG valuable stays encrypted. This eliminates one of the biggest regulatory blockers to enterprise AI adoption.
Healthcare
- By converting sensitive electronic health records into encrypted vector embeddings, multi-hospital systems can run AI analytics without the risk of exposing Protected Health Information (PHI). This method prevents the reconstruction of original data from database leaks or memory dumps, providing a direct HIPAA compliance win and clearing the path for real-world clinical decision support at scale.
Manufacturing
- Automotive manufacturers can securely optimize supply chains with AI while protecting supplier data and design intelligence. Competitors can’t reverse-engineer sensitive relationships from a leaked database, and engineers keep the same fast, seamless AI workflows they expect. Compliance with NDAs is built in by design.
Legal
- Top law firms can search across privileged communications and case strategies with confidence. Even if the database is breached, attackers cannot reconstruct client communications from encrypted vectors. This preserves attorney–client privilege in AI systems - solving a risk traditional legal tech never had to consider.
Getting Started
Cyborg Enterprise RAG Blueprint is available today on build.nvidia.com. Deploy the complete, enterprise-ready solution with CyborgDB's encrypted vector indexing & retrieval in minutes:
System Requirements:
- Docker deployment: 2x NVIDIA H100 or 3x NVIDIA A100 GPUs minimum.
- Kubernetes deployment: 8xH100-80GB or 9xA100-80GB.
- Alternative: Use NVIDIA NGC-hosted NIM with 1 NVIDIA GPU for CyborgDB acceleration.
- OS: Ubuntu 22.04.
What's Included:
- NVIDIA AI software (NeMo Retriever, Llama Nemotron 3.3).
- CyborgDB with NVIDIA cuVS GPU acceleration.
- NeMo Retriever multimodal PDF parsing and NeMo Guardrails.
- OpenAI-compatible APIs and sample UI.
- Production deployment configurations for Docker and Kubernetes.
Security Guarantees:
- Zero plaintext exposure in memory, logs, or caches.
- Forward-secure against future key compromise.
- No reconstruction possible from encrypted vectors.
- FIPS 140-2 & 140-3 validated cryptography.
Visit build.nvidia.com to access the blueprint and deployment guides. Happy building!








